Recovery of AOL PFC (Personal Filing Cabinet) Email Messages
Introduction
The use of electronic mail (email) as a mode of communications for both formal and informal purposes has increased considerably over the past decade. As such, the opportunities for the criminal element of society to make use of this facility have also widened making it commonplace within a digital forensics examination to review email content. Not so long ago, one email client which increased in popularity (particularly amongst paedophiles) in the United Kingdom was that provided with America Online (AOL).
Email extraction and analysis causes significant problems for digital forensic examiners. Almost all of the forensic software designed for extracting email is tailored for dealing with mail-store files which are intact. This means that they have not been designed to extract email data from the other areas of a suspect hard drive such as, unallocated clusters, cluster slack, page files, hibernation files and other binary source files. They have also not been designed to extract data fragments when the mail-store index has been overwritten.
From an evidential point of view, it is likely that a large quantity of email evidence is not being extracted. In addition, as there is limited documentation available regarding the proprietary binary file structures, there is wide variance in the output from many of the commercial forensic tools currently available.
AOL Email Client
In complete contrast to the wealth of software resources available for Microsoft Outlook Express, there are limited resources available for the file format of the AOL Personal Filing Cabinet (mail-store file) and email client.
There are numerous commercial companies offering a service to convert AOL Personal Filing Cabinet files into other mail-store formats, however, this is not a forensic service. A recent search revealed one company offering to convert a single PFC mail-store file for $200 US.
The AOL Email client stores data from individual email messages in a binary file generally known as the PFC (Personal Filing Cabinet). This file has no extension. In a typical Microsoft Windows XP system, the folder structure and mail-store files are stored within the user profile as shown below. The organize folder holds the mail-store data and has a structure which is in a similar format through various versions of the client. In this example, you can see a single screen name (this is an AOL term for a user) in use.
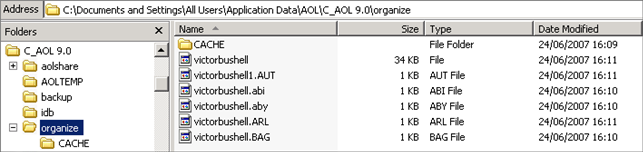
Figure 1
The data for this version is stored within an organize folder within the “All Users” Windows profile. The organize folder can support and store multiple screen names. The individual files for a screen name are shown below:
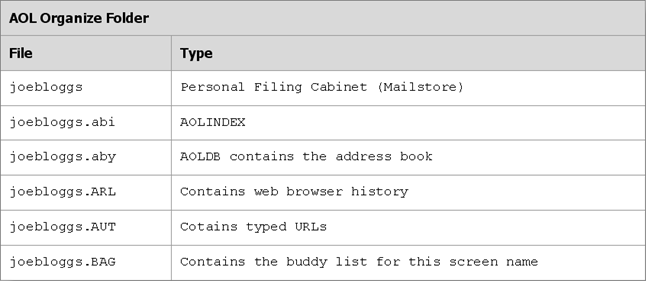
Figure 2
With regards to email messages, the main file of interest is the Personal Filing Cabinet (PFC). This is a binary file which contains a number of different AOL objects such as Favourite Places, Away Messages, Stored Email Messages, Newsgroup Postings and Download Manager information.
With AOL version 7.00 and above, the body of the email is compressed using ZLib. This causes a problem for the forensic examiner as traditional keyword searching will not be successful without decompressing the data first.
Recovery of AOL (Personal Filing Cabinet) Email Messages
Digital Detective’s forensic data recovery software Blade® contains a Professional Recovery module which has been designed to recover AOL email messages from a number of sources.
The Professional Recovery Module has the ability of recovering live and deleted email messages (including attachments) whether directly from a Forensic image (such as an Encase® e01 compressed image) or a physical disk / volume. The output from the software allows the forensic investigator to identify the exact location the data was recovered from.
The carving engine for this Module is the result of numerous years research and development. It was originally released in the Digital Detective product EMLXtract. When this software was released to law enforcement in 2004, it was the first software product to recover AOL email messages from an image or physical/logical device (as opposed to a single PFC File). When compared against other tools, this software recovered more email messages than any other. It works particularly well against corrupted data when many other tools fail to recover anything at all.
The research and development that went into recovering AOL email messages from a forensic image took a considerable amount of time. AOL email messages contain many different elements such as compressed and non-contiguous data blocks. Embedded attachments can be split and have to be stitched back together. When this module was originally designed, the goal was not to recover live and deleted email messages from a Personal Filing Cabinet, but to be able to recover emails from a disk image. This functionality was originally released to Police Forces all around the world as a tool called EMLXtract.
Through research and development, the recovery engine has been enhanced further and is now part of Blade®. The following video shows the extraction and examination of AOL email messages from a segmented disk image. Figure 3 shows a recovered email message from Blade® Professional.
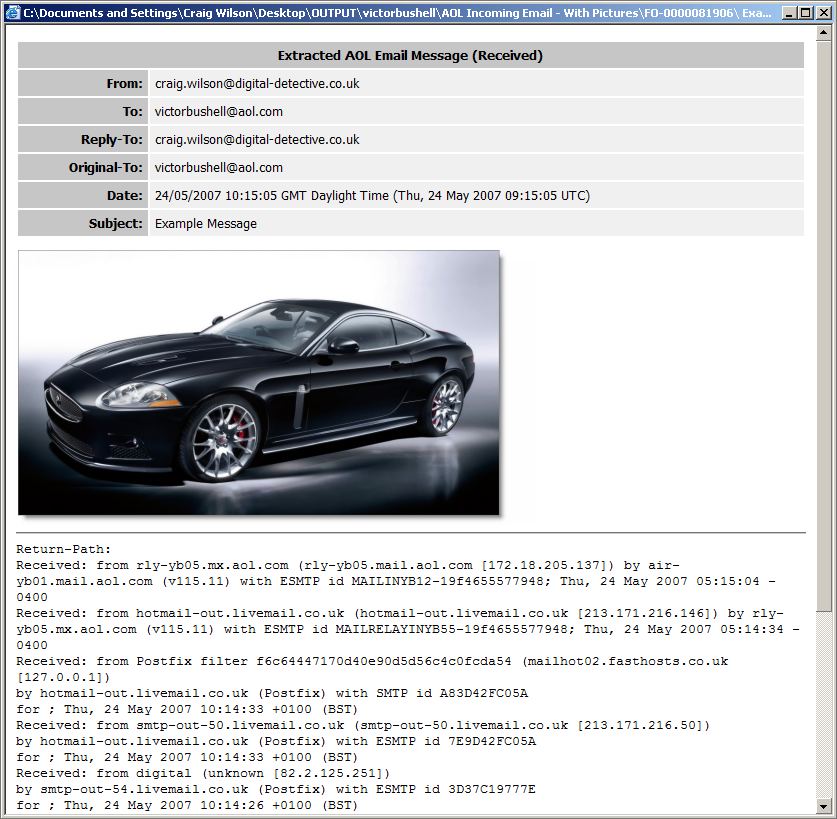
Figure 3
As Blade® process the source image, it recovers individual messages and converts them into an HTML representation of the original message. This includes decompressing the Zlib content and rebuilding the original attachments. The physical location of the original email is identified by Physical Sector and Sector Offset. The easiest way to use Blade® in a forensic examination is to simply point it at a forensic image of the original device.


